Why Plugin, Theme & Addon Authors Should Join A Vulnerability Disclosure Program
Does WordPress have a security problem? Yes, just like every other application on the internet. But there are two important considerations:
First, WordPress powers millions of websites. Each one is, effectively, a separate application managed by different people and teams.
Second, WordPress core is extended through a modular plugin architecture, making it a ‘composite’ platform that is the sum total of many smaller applications.
The point is that the same flexibility and extensibility that make WordPress so powerful also make it more exposed to attacks – which is why a Google News search for “WordPress” often reads like a security breach log.
So, what should we – the WordPress ecosystem – do about it?
As a marketer, I think we should push out more positive stories about WordPress to dilute the negative ones. I also think the project should invest in good old-fashioned PR to counter the “WordPress-is-not-secure” narrative.
But that alone doesn’t make WordPress more secure – and improving security is the real objective here. And it’s not just about securing WordPress either.
You Don’t Just Need Security. You Need Disclosure.
I’m not going to cover WordPress security best practices here – plenty of expert resources already exist, starting with WordPress.org’s guidance on keeping WordPress secure, and Patchstack’s resources covering WordPress in their Academy.
Instead, I’m going to focus on Vulnerability Disclosure: the process of reporting and resolving security issues in plugins, themes, or WordPress core.
If you’re a plugin or theme developer – or you create WPBakery addons – disclosure matters because:
- It reduces exposure and time to patch
- It holds you accountable, but also helps you stay compliant with local security laws and regulations
- It enables timely delivery of security updates
- It improves trust and resilience across the ecosystem
It’s also a selling point. Put yourself in your customer’s shoes: would you rather buy from a company that operates a Vulnerability Disclosure Program (VDP) – or one that doesn’t?
Non-Disclosure Can Cost You
As of now, there are no public examples of WordPress product companies being held legally liable for a security breach or for failing to disclose one. But that doesn’t mean it won’t happen.
In Australia, for instance, the Notifiable Data Breaches (NDB) scheme requires organizations to notify both affected individuals and the Office of the Australian Information Commissioner (OAIC) in the event of a qualifying data breach. Non-disclosure can lead to significant fines, as several telecom companies have discovered. You should check the laws in your region to understand your specific legal obligations and risks.
Reputation matters too. If your business is seen as secretive or irresponsible with security, it can seriously damage customer trust.
How Joining a Vulnerability Disclosure Program Helps
VDPs are run by security platforms, government agencies, nonprofits, and private organizations. They offer a framework for managing vulnerability reports through defined policies and communication channels, including:
- Receiving reports
- Validating and triaging issues
- Coordinating a fix or mitigation
- Optionally disclosing the issue publicly
- Acknowledging or rewarding the reporter (sometimes)
A quick note on public disclosure: it should only happen when it’s safe to do so. In some cases, it may be a better option not to disclose a vulnerability, depending on the risks and legal implications of doing so.
The goal of a VDP is to make sure vulnerabilities are handled correctly, by the right people, and in a timely way.
If you run a WordPress product business, you likely already follow development and deployment security best practices. A VDP complements these efforts by offering a structured and trusted pathway for vulnerability reporting – and a process designed to manage them efficiently.
Benefits of a VDP:
- Improved security through community involvement – faster, broader detection = fewer incidents
- Risk reduction and compliance readiness – helps meet legal and regulatory requirements, including the EU Cyber Resilience Act
- Stronger trust with users and partners – shows you’re transparent and proactive about security
- Streamlined workflows – structured, trackable reporting beats ad hoc emails and GitHub issues
- Reputation boost – demonstrates leadership and accountability, especially in competitive markets
Patchstack’s Managed VDP
This is the program we’ve enrolled in and are familiar with, though it’s not the only option. Patchstack describes it as a “security and compliance platform for open-source vendors,” so it’s not WordPress-exclusive. The “m” stands for “Managed” – their team triages and validates vulnerabilities before passing them on to vendors.
Once you join, you’ll be asked to create or link to a vulnerability reporting page that includes a submission form.
Here’s what our own vulnerability reporting page looks like, featuring links to our three products:
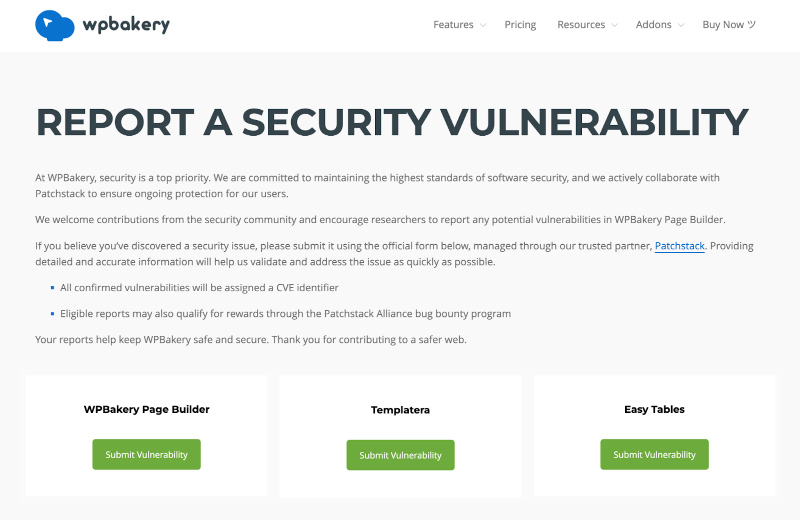
To report a vulnerability, a user clicks through to the respective landing page on Patchstack’s website where you can submit details of the issue.
You can also join their Bug Bounty program to be rewarded for the vulnerabilities you find.
Compliance with the The Cyber Resilience Act (CRA)
In Q4 2024, the Cyber Resilience Act (CRA) established mandatory requirements for software support and vulnerability disclosure for all commercial software distributed within the European Union.
Patchstack addresses this by serving as a specialized intermediary, simplifying and managing the vulnerability disclosure process on behalf of WordPress plugin and theme developers.
Cleaning Up the WordPress Plugin Repository
In October 2024, as part of Cyber Security Month, Patchstack launched an initiative to clean up the WordPress plugin repository by identifying and removing outdated or vulnerable plugins. Over 1,000 plugins and themes were removed, and reaching their authors proved difficult.
More specifically, in 1,162 of 1,571 cases, Patchstack had to contact the WordPress Plugin Review Team to try to reach the developers. Over 900 developers did not respond at all. It remains unclear whether they will address or fix the issues – or notify affected users. If these developers had been part of a VDP, coordinating disclosure would have been significantly easier.
For context:
- Cross-Site Scripting (XSS) was the most common vulnerability, found in 67% of cases
- 48% of vulnerabilities had a CVSS score of 7.1, categorized as high severity and capable of leading to serious impacts such as:
- Gaining unauthorized access
- Compromising data confidentiality, integrity, or availability
- Escalating user privileges
Kudos to Patchstack and the Bug Bounty participants for helping make WordPress safer – and hopefully reducing the number of security breach headlines in Google News.
Getting Started with Patchstack’s mVDP
As mentioned, it’s not the only VDP available but the one we chose, but it’s always a good idea to research different options.
We hope that WPBakery developers who have created plugins and addons for our products will join one and embrace security and disclosure best practices.
Joining Patchstack’s mVDP is free, but they also offer a paid tier that offers a more comprehensive set of tools and reports, including AI-powered code review. To join, head over to Patchstack, create a vendor account and follow the instructions.